Data Governance For AI Agents, AI Services and Third Party Flows
Book a Demo Today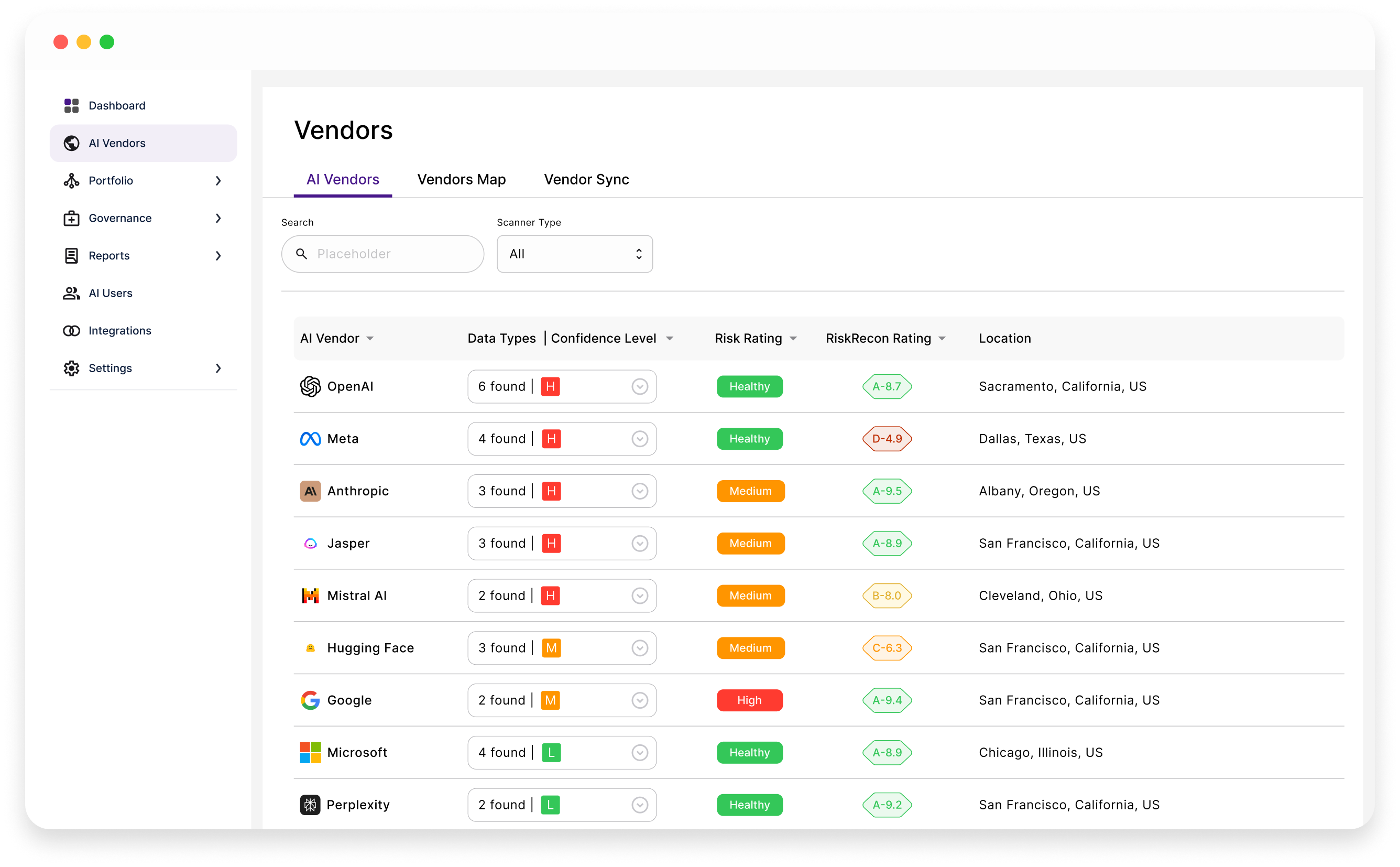





Forget about time-consuming installations. Riscosity makes securing your AI usage seamless, quick, and scalable, protecting your data and ensuring your operations run smoothly.

Get started without writing a single line of code. Riscosity's intuitive interface lets you manage and track AI usage effortlessly. No technical expertise needed, just plug in and go.

Eliminate the need for complex installations or software agents. Riscosity seamlessly integrates into your system, providing hassle-free monitoring and security.

Own your data. Whether hosted on your infrastructure or a trusted cloud provider, Riscosity ensures that your data stays private and protected.
Riscosity automatically detects and catalogs every AI vendor your applications and end-users communicate with, even the ones you weren’t aware of. Get real-time insights into where your data is flowing and take control of vendor risks.
Learn more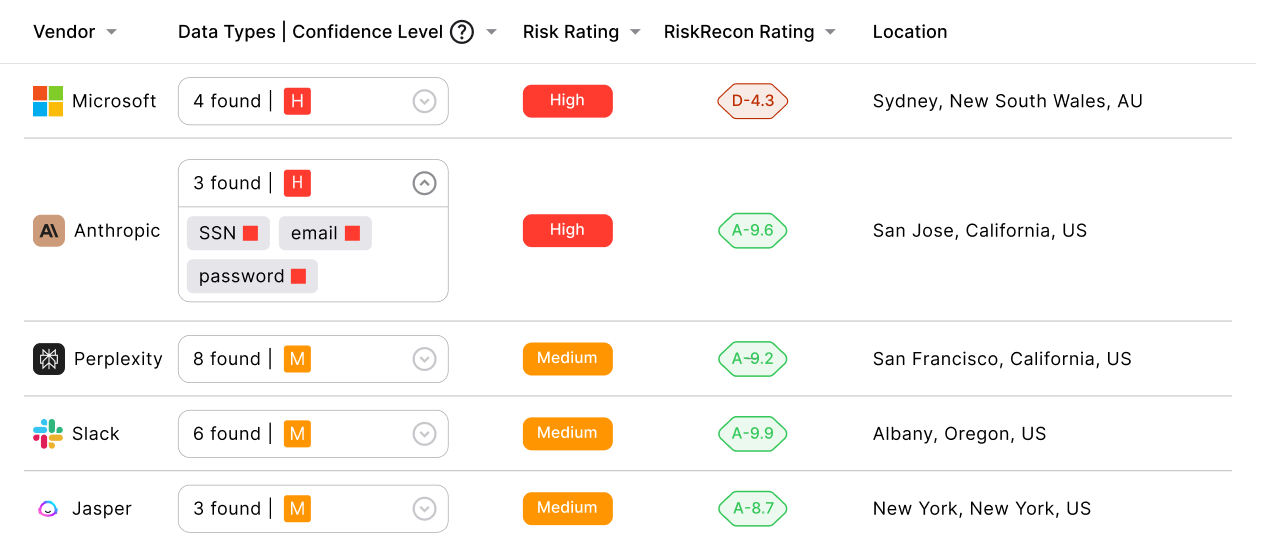
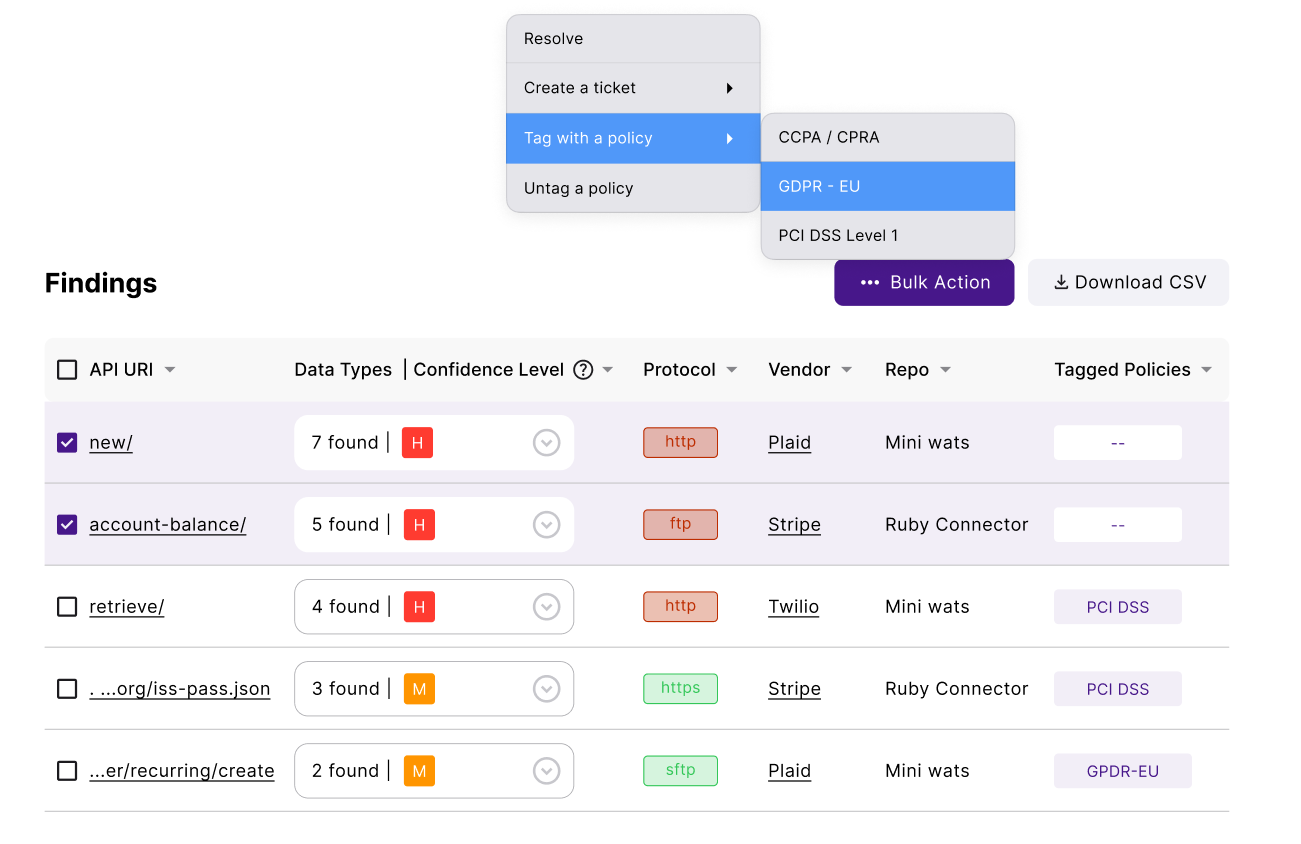
Track API requests across your infrastructure, from internal to external AI services. Instantly flag shadow AI usage and unusual traffic to prevent unauthorized data flow.
Learn moreEnsure that sensitive data — PII, PHI, financial details, and secrets — never reaches unauthorized AI vendors or is exposed by end-users to AI chatbots. Stay compliant with GDPR, PCI, ISO 27001, and the growing list of compliance standards and laws.
Learn more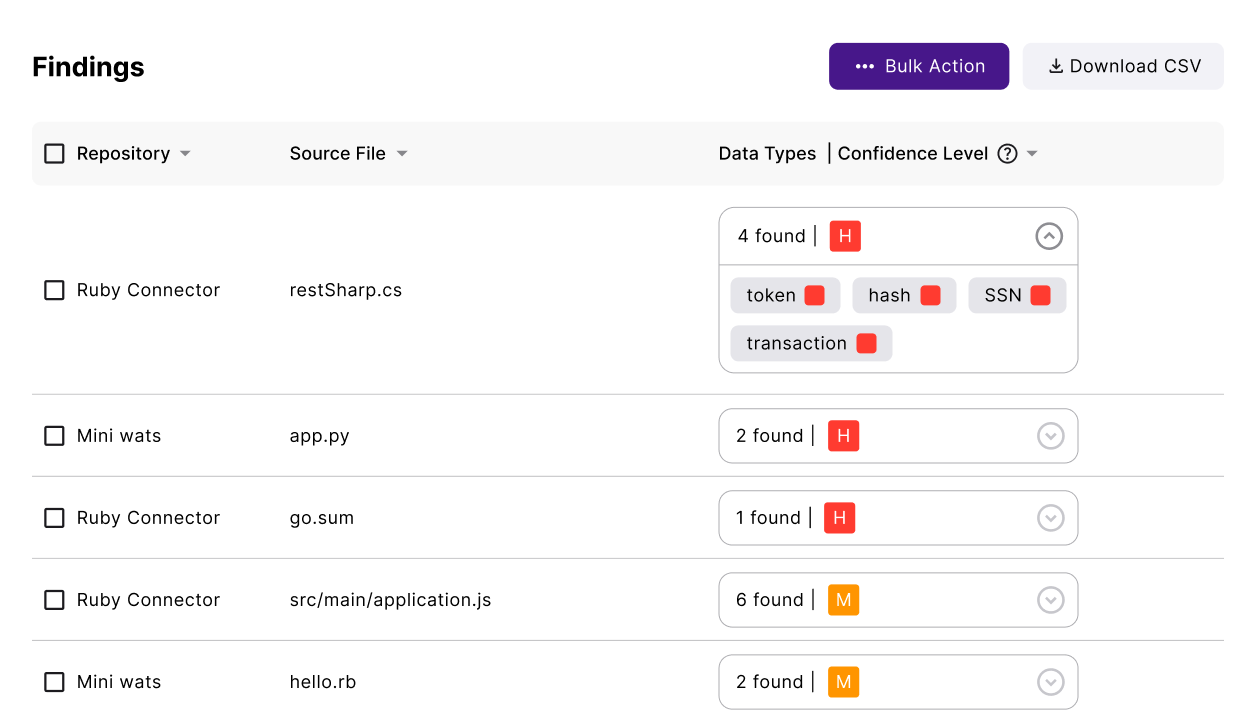
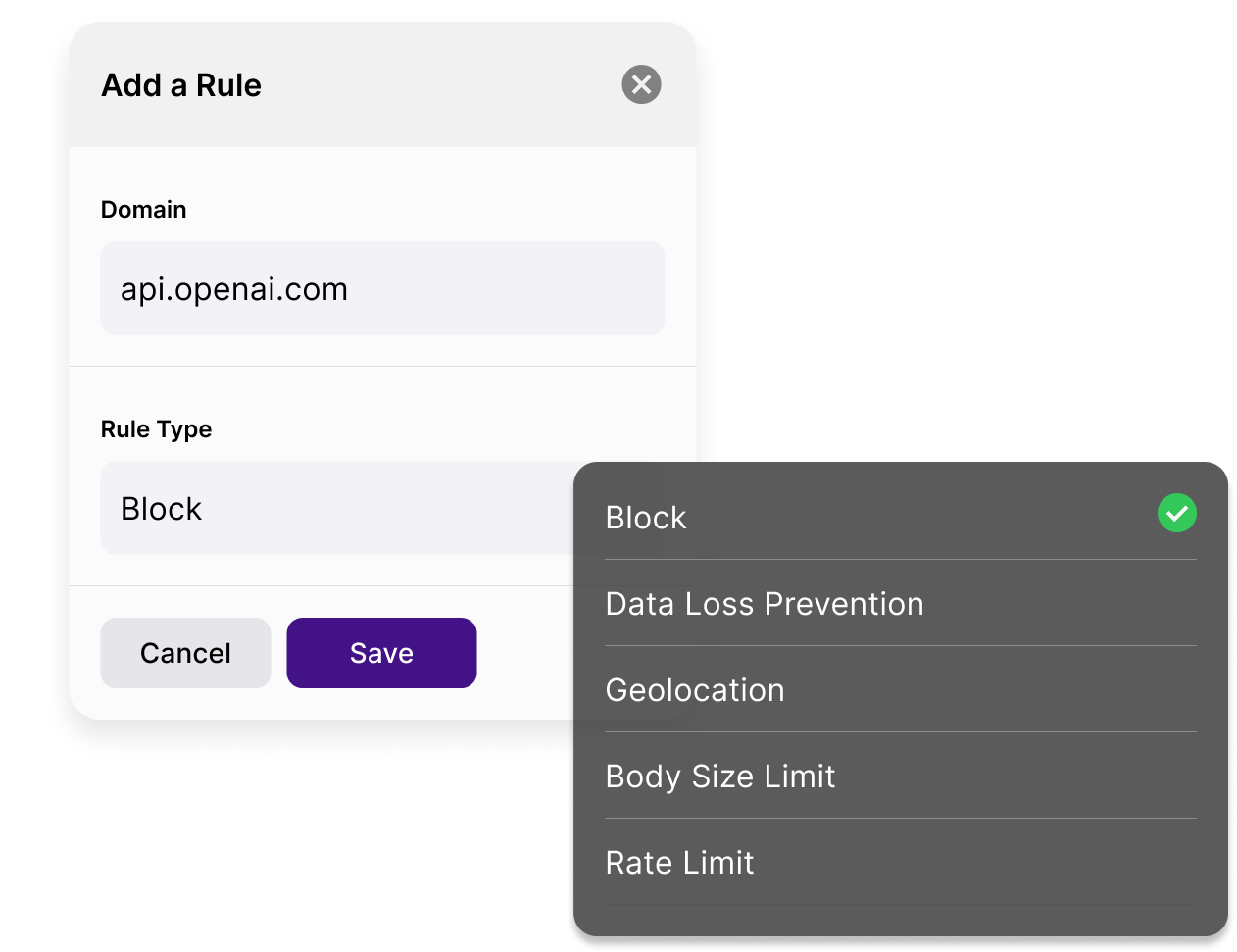
Riscosity’s AI firewall helps you block unauthorized requests, redact sensitive fields, and trigger real-time notifications for anomalies. Customize policies and gain sovereignty over your data in transit
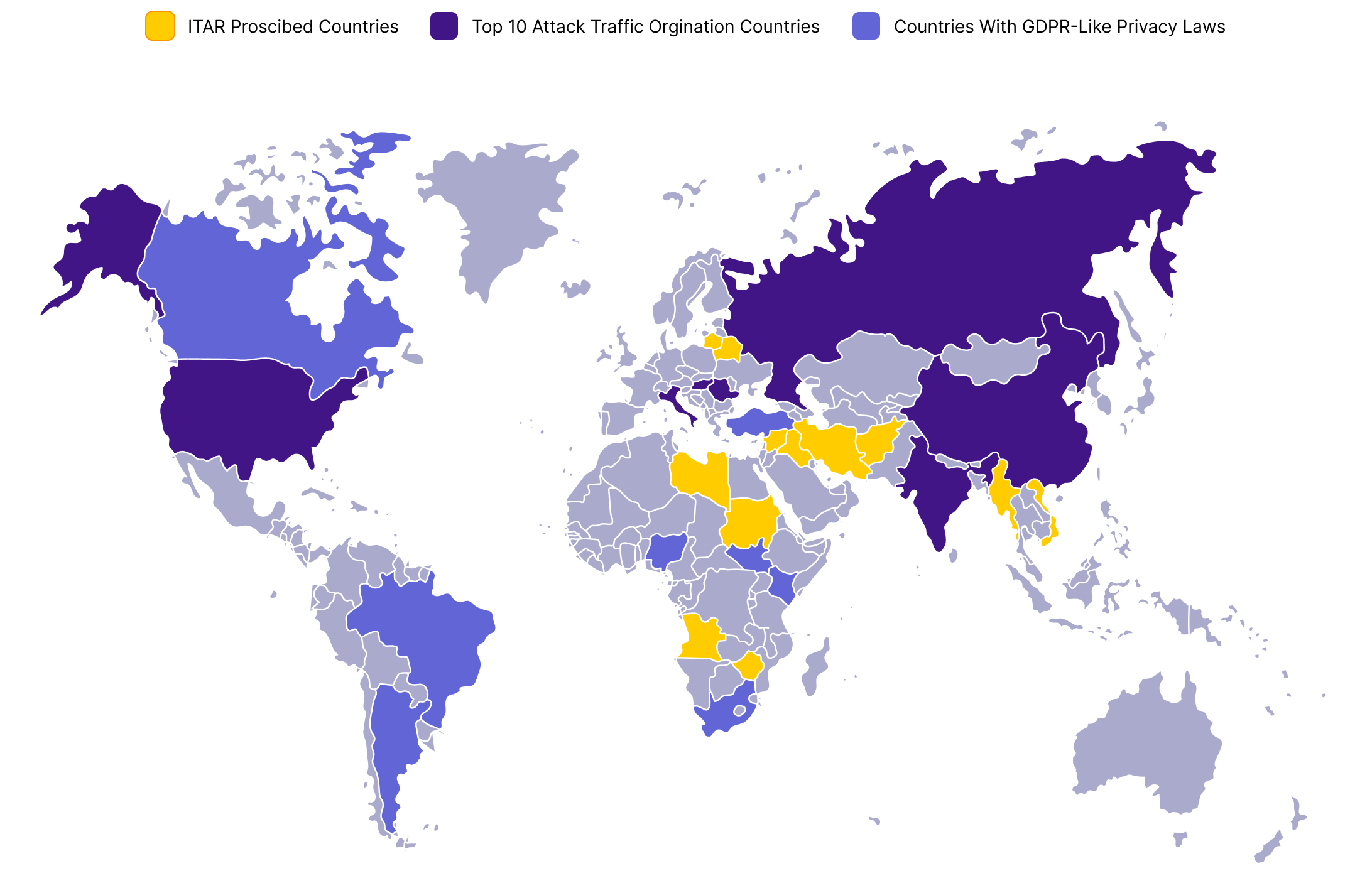
Learn moreDefine geo-fencing rules to govern where your data can go. Manage cross-region AI usage directly within your infrastructure and maintain compliance with local and international data privacy regulations